
What is Cross Site Scripting(XSS) and How to Prevent
Hello everyone, in this article we are going to talk about Cross Site Scripting. XSS stands for Cross Site Scripting. In this article we are going to use XSS term instead of Cross Site Scripting. After explanation we will talk about how can we protect our website from XSS attacks.Let's get started.
Firstly What is Cross Site Scripting?
XSS is a injection type of web attacks. With XSS the attacker injects their malicious script to the target webpage. XSS attacks takes place to the target website or the target user via web browser application. Attackers use the webpages inputs to locate their malicious scripts.
When the attacker locate a malicious script for the other users, the other users web broser will download this script. The target browser will see this related script from a thrust source and download it. With these script the attacker can reach any cookies, sessions and HTML page contents even they can make changings on them.
There are some kind of XSS Attacks:
- Reflected XSS : Attack script comes from directly HTTP responses.
- Stored XSS : Attack comes from directly Web Site Database.
- DOM-Based XSS : The attack comes from client side elements instead of server.
Reflected XSS
Reflectd XSS is the simplest way of the XSS attacks. This type of attack comes from directly HTTP response. This attacks works in the page as normal Javascript codes. The webpages will run the javascript codes when see it. So, if you write a code between script tags at anywhere of the page, the browser will this script.
Let's see how it works below :
Generally at websites the search inputs will redirect the page to the search page with the search parameters like below:
http://website.com/search.php?search.php?key=search_parameters
And let the page show the page data like below:
echo "Search : " . $_GET['search_parameters'] ;
.
.
.
show_search_results($_GET['search_parameters']);
While printing the parameter at the screen it directly write what the attacker write. If we do not protect our website the attacker will probably write a scipt on the input box and that script will run when page loaded.
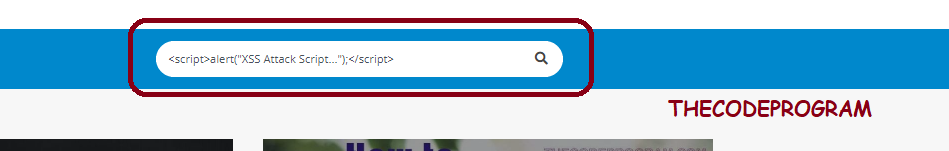
http://website.com/search.php?search.php?key=<script>alert("XSS Attack Script...");</script>
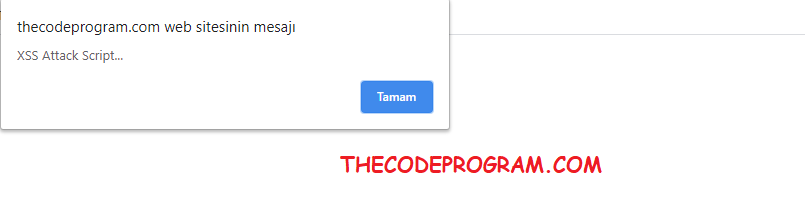
When this page worked at the screen this script will be worked. The attacker will probably write the malicious code instead of this simple alert command.
Stored XSS
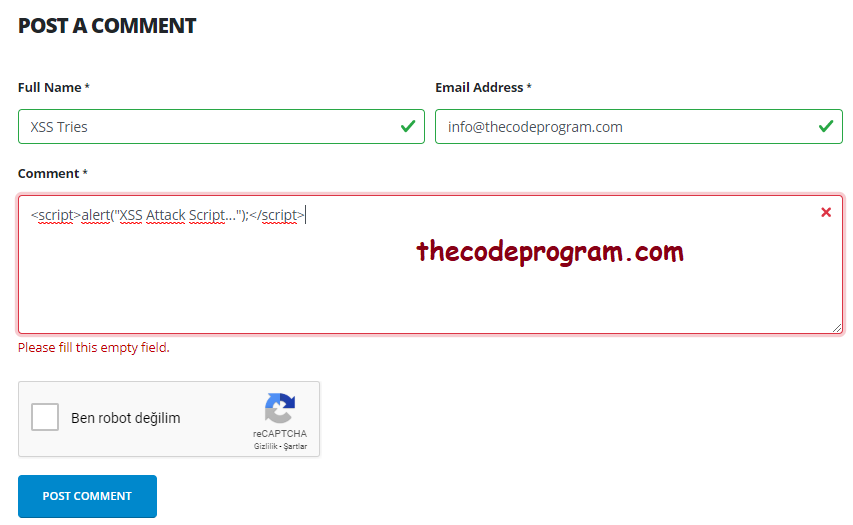
This attack comes from database with the HTTP response. These attacks comes from unthrusted HTTP sources. These malicious may be added to the database with user name, nicknames comments or anything else that the attackers add into the website database. When these scripts run on the website with datas from database the attacker reached what it wants.
Via above comment line the xss will be added to the database and if the comment will be showed at the page the code will directly run when the page loaded.
DOM-Based XSS
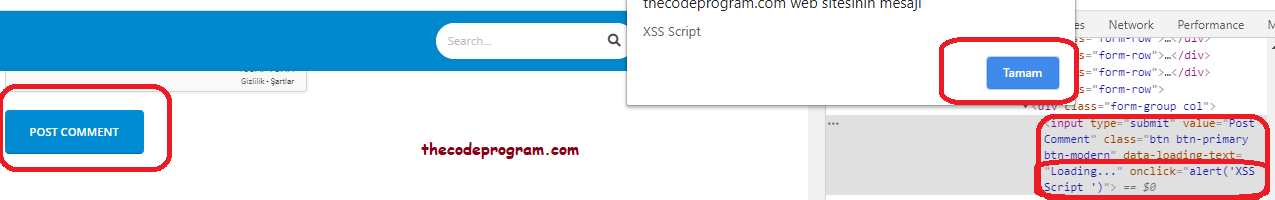
When the application write somethings into a DOM element of the page via javascript or the some requests this will happen. For example the button element has an onClick action. Anyone can make some changings on the DOM elements. For example after page is loaded and attacker can change somethings on the page.
Normally, there is no onClick area on above image DOM element. I manually added this code block via Inspect Element of the browser. And then when we clicked this element after submitted the changings, written script will be worked. Below Image you can see it :
You can do with XSS:
- Perform some operations that normal users can do.
- Attacker can log the victim login informations with typing or clicking the LogIn button.
- The attacker can make a flooding via this victim computer.
- Attacker can inject a trojan into the website.
- Attacker can mask the attack via XSS.
How to prevent XSS Attacks:
- As a developer filter every data that inputted via the searchbox or commentbox like them.
- Use the Content Security Polichy to reduce XSS vulnerability.
- Specify the Content-Type of the HTTP response. With this the browser will interpret correctly the data.
- In PHP you can add the some lines to the .htaccess, I shared them below.
- You can encode some dangerous characters.
You can add below lines to protect with .htaccess for PHP web sites.
<IfModule mod_headers.c>
Header set X-XSS-Protection "1; mode=block"
Header always append X-Frame-Options SAMEORIGIN
Header set X-Content-Type-Options nosniff
</IfModule>
That is all in this article.
Have a good XSS Protection.
Burak Hamdi TUFAN.





Comments